Authentication vs Authorization vs Access Control
This is a short article on the differences between three important and fundamental security concepts that are often confused. The difference between authentication, authorization and access control is often not understood properly, and sometimes they are thought to be the same thing or the terms are used interchangeably.
Perhaps this is because the processes of authentication, authorization and access control often appear to happen at the same time from an end user’s perspective, and as one single process. But it is important to understand the distinction when designing the security framework for a software application, so here we provide a clarification of these distinct concepts and provide an explanation of how they would be applied to a typical software application or website.
Authentication
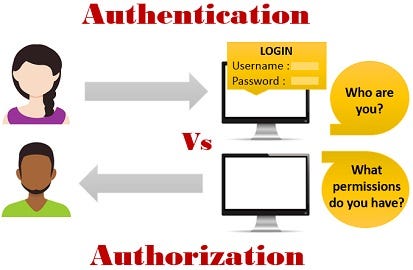
Authentication is a process by which you verify that someone is who they claim they are.
This usually involves asking the user for a username and a password, but it can include any other method of demonstrating identity, for example a smart card, a PIN number, a secret code sent in a letter in the post, a fingerprint scan, and so on.
In order to perform authentication, a user must already have an account created in a system which can be interrogated by the authentication mechanism, or an account must be created as part of the process of the very first authentication.
The output of the authentication process is usually a binary “yes or no” results – either the user is who they say they are, or they are not (a “maybe” would be treated as a “no”).
Authorization
Authorization is the process of establishing if the user (who is already authenticated), is permitted to have access to a resource. Authorization determines what a user is and is not allowed to do.
The level of authorization to give a user is determined by examining the additional properties (metadata) associated with the user’s account. For example, data associated with a user may indicate if they are a member of a given group such as “Administrators” or “Customers”, or it may indicate if they have paid a subscription for some paid-for content, or it may indicate that they are still within the 90 day period of a free trial.
Authorization also includes an Authorization Management component, which is a system that provides the functionality to create the authorization rules.
Access Control
Access Control is the process of enforcing the required security for a particular resource.
Once we know who a user is, and we know what authorization level they have and what we should and should not give them access to, we need to physically prevent that user from accessing anything that they should not be able to. Access Control can be seen as the combination of Authentication and Authorization plus additional measures, such as clock- or IP-based restrictions.
In the context of a web or software application, access control may be implemented using bespoke logic, security features of the development framework being used, file permissions, URL access lists, or many other mechanisms. Note that lack of adequate access control is more often the cause of security vulnerabilities in applications than faulty authentication or authorization mechanisms, simply because access control is more complex to implement and becomes more complex as the application being secured becomes more complex itself.
Further Reading
The following articles are worth reading for further details on the subject. In particular, Authentication and Authorization and often combined with Accounting (that is, the logging of information relating to Authentication and Authorization) to form “AAA” – Authentication, Authorization and Accounting.


Comments
Post a Comment